The High and Critical Vulnerability tiles display the number of vulnerabilities with the corresponding severity detected within the core product or any of its dependencies. Selecting the tile will display a modal that provides high-level details on each of the vulnerabilities and the complete vulnerability scan data in JSON format.
Vulnerabilities within the core product can be detected when a product name and version have been provided in the project settings and exists within NVD's CPE Dictionary. If a CPE does not exist for the product, you may submit one to NVD.
Ion Channel's vulnerability data is obtained from the National Vulnerability Database (NVD) and npm Security Advisories.
NVD Vulnerabilities
The severity of vulnerabilities obtained through NVD is assigned using the Common Vulnerability Scoring System (CVSS). If CVSS v3.0/3.1 ratings are available, Ion Channel will use those severity ratings to determine if a vulnerability has a high or critical severity. Otherwise, CVSS v2.0 severity ratings will be used.
The Critical Vulnerabilities tile will provide a count of any vulnerability with a CVSS v3.0 rating of 9 and higher. The High Vulnerabilities tile will provide a count of any vulnerability with a CVSS v3.0/3.1 rating of 7 - 8.9 or a CVSS v2.0 rating of 7 or higher (when v3.0/3.1 is not available).
| CVSS v2.0 Ratings | CVSS v3.0/3.1 Ratings | |||
| Severity | Base Score Range | Severity | Base Score Range | |
| Low | 0.0 - 3.9 | None | 0.0 | |
| Medium | 4.0 - 6.9 | Low | 0.1 - 3.9 | |
| High | 7.0 - 10.0 | Medium | 4.0 - 6.9 | |
| High | 7.0 - 8.9 | |||
| Critical | 9.0 - 10 | |||
npm Vulnerabilities
Vulnerabilities obtained from npm can have one of four severity ratings: low, moderate, high, or critical. Npm vulnerabilities of high or critical will appear in those respective tile counts. For numerical scoring purposes, Ion Channel will apply a score with the following.
| npm Vulnerabilities | |
| Severity | Assigned Severity Score |
| Low | 1.0 |
| Medium | 5.0 |
| High | 7.0 |
| Critical | 10.0 |
Governance:
The Critical/High Vulnerability rule governs the pass/fail status of the High and Critical Vulnerabilities scan. When this rule is enabled in the governing ruleset, the analysis will only pass if the number of vulnerabilities with a severity of high or critical is less than the threshold assigned to that rule.
Vulnerability Details:
By selecting the High or Critical Vulnerabilities tiles and viewing the Details tab, you will find a list of the vulnerabilities matching the severity of the tile, a description of the vulnerability, and a list of the software products affected by the vulnerability. If more detailed information about each vulnerability is desired, the JSON data in the Data tab can be searched for the vulnerability name.
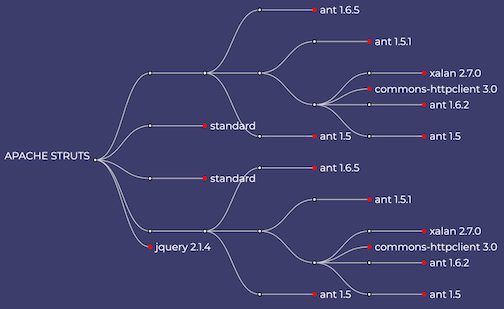
Dependency Tree:
By selecting the High or Critical Vulnerabilities tiles and viewing the Tree tab, you will find a tree that presents all dependencies affected by a vulnerability and the path taken for that dependency to be introduced into this project. This tab will only be present when vulnerabilities with a severity matching the tile are present.
Vulnerable dependencies are represented with a red dot along with the dependency name and version. White dots represent dependencies within the path leading to a vulnerable dependency. Hovering over any affected dependency will display all vulnerabilities that affect that dependency and highlight identical dependencies within the project.
Tile Statuses:
Passing: The sum of high and critical vulnerabilities is less than the maximum allowed by the governing ruleset.


Failing: The sum of high and critical vulnerabilities exceeds the maximum allowed by the governing ruleset.
.png)

Not Evaluated: The governing ruleset is not configured to consider the number of vulnerabilities present and the scan has been completed.


Error: An error occurred during the scan or analysis. Selecting the tile will provide information on the cause of the error.

